On June 6, 2025, President Trump issued an Executive Order (“Sustaining Select Efforts to Strengthen the Nation’s Cybersecurity and Amending Executive Order 13694 and Executive Order 14144”) (the “Order”) that modifies certain initiatives in prior Executive Orders issued by Presidents Obama and Biden and highlights key cybersecurity priorities for the current Administration. Specifically, the Order (i) directs that existing federal government regulations and policy be revised to focus on securing third-party software supply chains, quantum cryptography, artificial intelligence, and Internet of Things (“IoT”) devices and (ii) more expressly focuses cybersecurity-related sanctions authorities on “foreign” persons. Although the Order makes certain changes to prior cybersecurity related Executive Orders issued under previous administrations, it generally leaves the framework of those Executive Orders in place. Further, it does not appear to modify other cybersecurity Executive Orders.[1] To that end, although the Order highlights some areas where the Trump administration has taken a different approach than prior administrations, it also signals a more general alignment between administrations on core cybersecurity principles.
The first section below provides a summary of revisions to existing federal government policy. The second section provides a chart of new directives to federal government departments and agencies.
Amendments to Prior Orders
The new Order seeks to amend existing federal government policies and regulations (as previously set by Executive Orders 14144 and 13694) to: (i) remove certain requirements for secure software development attestations, directives tied to acceptance of digital identity documentation, and certain technical hardening measures for identity verification and email encryption, and (ii) more expressly focus cybersecurity-related sanctions authorities specifically to foreign (as opposed to any) cyber threat actors that target U.S. critical infrastructure.
- Secure Software Acquisition: The Order removes certain requirements relating to secure software attestations that federal government contractors must submit to contracting agencies. This includes elimination of the requirement that attestations must be in machine readable format. This also includes elimination of the directive for centralized validation of software attestations by the Cybersecurity and Infrastructure Security Agency (“CISA”). Likewise, the associated directive to the Federal Acquisition Regulatory Council to amend the Federal Acquisition Regulation (“FAR”) to incorporate those requirements has also been eliminated. The Fact Sheet accompanying the Order notes that one goal was to eliminate requirements for “imposing unproven and burdensome software accounting processes that prioritized compliance checklists over genuine security investments.” However, the Order did not address the more general requirement for software attestations that appeared in the May 2021 Executive Order No. 14028 “Improving the Nation’s Cybersecurity,” as implemented through Office of Management and Budget (“OMB”) Memoranda (M-23-16 and M-22-18) and the CISA Common Self-Attestation Form. Thus, it is unclear whether this Administration will promulgate regulations that would implement those requirements from the 2021 EO within the FAR, suspend any requirement for further attestations until NIST issues the final update of its Secure Software Development Framework required by the Order, eliminate the requirement for attestations altogether, or impose attestation requirements on a contract-by-contract basis and continue to maintain the CISA repository for those forms.
- Solutions to Combat Cyber Crime and Fraud: The Order removes prior directives for federal government agencies to accept digital identity documentation (e.g., digital driver’s licenses) for public benefit programs.
- Identity Technologies: The Order removes prior requirements for the Federal Civilian Executive Branch (“FCEB”) to deploy commercial phishing-resistant standards such as “WebAuthn.”
- Email Encryption: The Order removes a directive to OMB to require the expanded use of authenticated transport-layer encryption (“TLS”) between email servers used by FCEB agencies to send and receive emails.
- Quantum Computing: The Order scales back quantum computing initiatives, included as part of National Security Memorandum 10 (“NSM-10”)(“On Promoting United States Leadership in Quantum Computing While Mitigating Risk to Vulnerable Cryptographic Systems,” May 4, 2022) implemented through OMB Memorandum (M-23-02), that required federal agencies to adopt post-quantum cryptography (“PQC”) as quickly as feasible and encourage technology vendors to do the same, as well as pushing for it being accepted internationally. The Order retains only a requirement for CISA to maintain a list of product categories where PQC-enabled tools are widely available.
- Artificial Intelligence (“AI”): The Order takes a different approach to previous policy, amending E.O. 14144’s existing approach to security with and within AI, and diverges from previously revoked E.O. 14110 (“Safe, Secure, and Trustworthy Development and Use of Artificial Intelligence,” October 30, 2023), which encouraged AI-driven collaboration across industry and had tasked federal agencies with aggressively exploring artificial intelligence for cybersecurity defense.
- Focus on “Foreign” Cyber Threat Actors: The Order amends existing cybersecurity-related sanctions authorities for malicious actors engaged in cyber-enabled activities that pose a threat to U.S. national security, foreign policy, economic health, or financial stability, including those targeting U.S. critical infrastructure, to limit these authorities to foreign malicious actors and thereby more clearly excluding domestic individuals or activities from the scope of the authorities. The accompanying Fact Sheet further explains that the focus on foreign malicious actors is to prevent “misuse” of the sanctions authorities “against domestic political opponents,” and clarifies that “sanctions do not apply to election-related activities.” The Order and the accompanying Fact Sheet do not provide any additional information about whether the amendments are intended to exempt foreign cyber operations directed at U.S. election activities, though the underlying sanctions authorities do still address malicious cyber-enabled activities that involve “tampering with, altering, or causing a misappropriation of information with the purpose of or that involves interfering with or undermining election processes or institutions.”
The Federal Communications Commission’s cybersecurity labeling program, Cybersecurity Labeling for Internet of Things (proposed rule, 47 CFR Part 8) has remained. This program was modeled after the Energy Star efficiency label and will certify internet-connected consumer products, such as IoT devices, based on whether they meet certain cybersecurity criteria verified by accredited labs.
Timeline of New Directives
The below table outlines the directives to federal government departments and agencies, including: the Departments of Commerce, Defense, Energy, and Homeland Security as well as CISA, OMB, the National Institute of Standards and Technology (“NIST”), the Office of the Director of National Intelligence (“ODNI”), the National Security Agency (“NSA”), the National Science Foundation (“NSF”), the Office of Science and Technology Policy (“OSTP”), and the Office of the National Cyber Director (“ONCD”).[2]
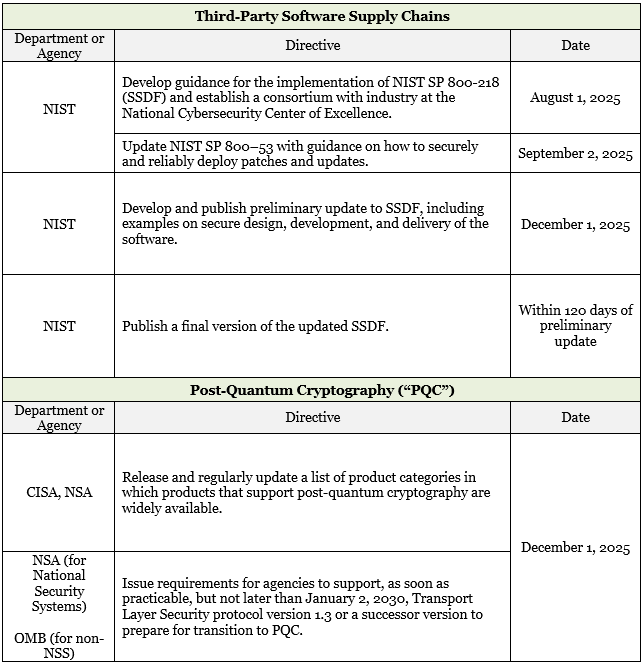
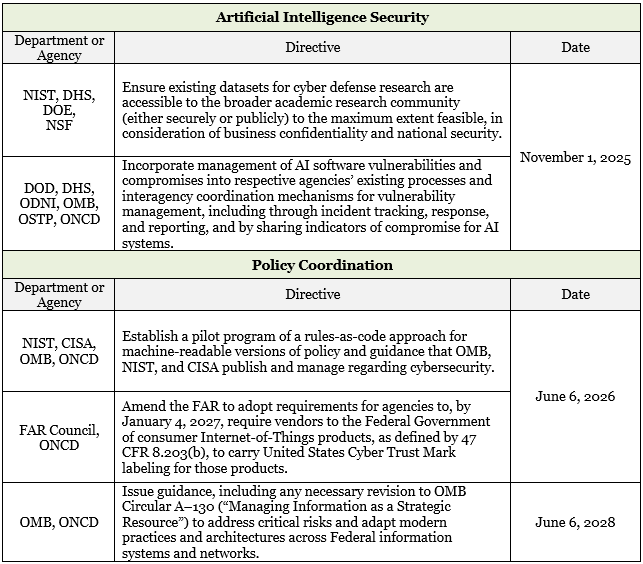
Table 1: Summary of directives to Departments and Agencies.
[1] Section 2 also provides, “Except as specifically provided for in subsection 4(f) of [Executive Order 14144], sections 1 through 7 of [Executive Order 14144] shall not apply to Federal information systems that are NSS or are otherwise identified by the Department of Defense or the Intelligence Community as debilitating impact systems.”
[2] For example, the Order does not rescind or modify Biden’s Executive Order 14028 (“Including Biden’s Executive Order 14028”).