Many CFOs continue to equate strong audit outcomes with effective fraud containment. In modern business environments, however, transactions move faster and approvals are increasingly distributed, meaning exposure is often identified only after financial scams and frauds have already occurred.
This delayed discovery is evident across organizations of all sizes. According to the 2025 Association of Finance Professionals Payments Fraud and Control Survey, nearly 79% of organizations reported actual or attempted payments fraud activity in 2024.
A 2024 survey of finance professionals in the U.S. and the U.K. by Medius, an AP automation solutions provider, revealed the extent of revenue loss due to invoicing fraud. It found that, on average, finance teams encountered 13 cases of attempted and 9 cases of successful invoice fraud per year, with an average loss of $133,000 in the U.S. and £104,000 in the U.K.
These losses underscore a harsh truth: actively combating financial scams and frauds requires earlier risk visibility than traditional, audit-led assurance models can provide.
Where Does Fraud Exposure Emerge in Mid-Market Finance Operations?
Even as mid-market organizations scale, finance teams continue to operate with lean staffing models, fragmented systems, and trust-based approval structures. At the same time, payment volumes accelerate while decision-making becomes more distributed. This combination causes fraud exposure to concentrate at approval and execution points, where speed outpaces real-time risk visibility.
- Payment assurance models built for lower volumes do not scale with modern transaction velocity.
- Invoicing fraud exploits fragmented vendor data and post-approval validation. When invoice verification occurs after approval or payment scheduling, fraudulent or manipulated invoices blend into routine payables activity, shifting discovery until after cash is committed.
- Trust-based authorization concentrates fraud risk at decision points. Business email compromise exploits approval models built on hierarchy and familiarity rather than independent verification.
- Financial statement fraud persists because assurance arrives too late in the reporting lifecycle. Unlike transaction-level schemes, financial statement fraud examples typically unfold over extended periods, exploiting weaknesses in reconciliations, overrides, and management judgment.
When fraud goes undetected across reporting cycles, the risk extends beyond financial loss. What begins as an operational failure can quickly trigger regulatory scrutiny and reputational damage, exposing organizations to financial fraud crimes driven by control breakdowns, not malicious intent.
Why Compliance-Oriented Controls No Longer Ensure Protection
Traditional fraud controls are built to detect issues after damage has occurred, whereas the prevention of financial fraud requires embedding risk awareness directly into everyday finance workflows. In this context, a practical financial fraud definition extends beyond intentional misconduct to include control failures that allow material misstatements or misuse of funds to persist – undetected.
However, most existing approaches were designed for slower, more predictable operating environments. As transaction volumes rise and finance processes become more distributed, these assumptions break down.
- Static control designs that do not adapt to changing behavior
As fraud tactics increasingly leverage automation, impersonation, and synthetic content, static controls struggle to adapt at the pace required, elevating the role of AI-driven detection in modern finance environments. - Manual oversight that does not scale with transaction volume
As transaction volumes grow and fraud tactics become more technologically sophisticated, relying on manual systems and checks increases the risk of missed signals and errors, leaving finance teams ill-equipped to detect or counter financial frauds in real time. - Delayed response that amplifies downstream impact
Late detection increases recovery costs and investigation effort, shifting the burden of response into business operations. - Evidence of execution without confidence in containment
Many control frameworks confirm that required steps were completed, but provide limited assurance that emerging fraud risk is being identified or contained before financial exposure occurs.
How Modern Finance Teams Actively Combat Fraud
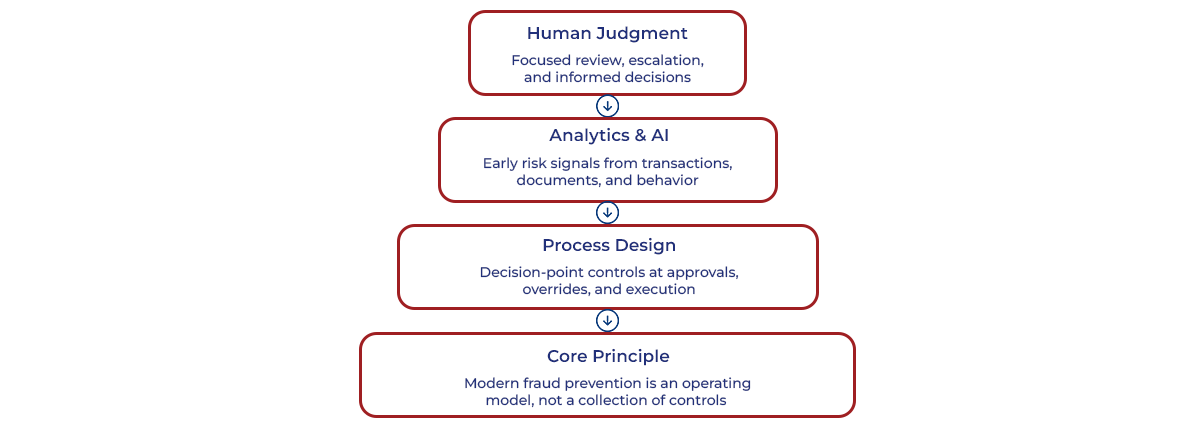
Modern finance teams are responding to fraud risk by redesigning fraud prevention, rather than adding more controls. Instead of post-transaction review and retrospective assurance, finance teams are re-engineering operations to identify fraud risk before transactions are authorized. This operating model shift prioritizes early intervention, preserves execution speed, and strengthens assurance.
Design Controls Around Decision Points
- Controls focus on approvals, overrides, and exceptions. These moments define financial commitment and represent the most effective points for risk intervention.
- Independent verification replaces trust-based authorization. This reduces governance gaps and limits exposure.
Enable Early Risk Signaling
- Risk signals surface during execution, not after reporting. Finance teams monitor behavior and patterns as activity progresses, allowing intervention before payment release or posting. This shift is increasingly enabled by AI-driven pattern analysis that can detect subtle behavioral anomalies in real time.
- Earlier visibility preserves decision optionality. CFOs can act while corrective action is still feasible, reducing recovery effort and downstream impact.
Preserve Speed Through Selective Friction
- Low-risk transactions proceed without added controls or review. Controls intensify only where risk concentrates.
- Automation accelerates standard execution while highlighting exceptions. Human judgment is applied selectively, strengthening prevention without slowing operations.
Tech-Enabled Finance Operations
- Automation standardizes execution and improves signal quality. By reducing manual variability in high-volume activities, automation creates consistent transaction and approval flows that can keep pace with increasing scale and velocity. This consistency strengthens data integrity and makes anomalies easier to detect, even as fraud tactics become more complex.
- Embedded analytics provide real-time validation. Financial fraud analytics, powered by machine learning, natural language processing, and generative AI, analyze transactions alongside unstructured signals such as emails, invoices, supporting documents, and approval notes. This enables finance teams to detect complex, coordinated fraud patterns and synthetic activity that would bypass rule-based controls and manual review.
- Oversight shifts from broad review to focused judgment. With analytics-driven exception reporting, finance teams move away from exhaustive manual checks and apply expertise selectively to higher-risk scenarios. This improves decision quality and responsiveness while preserving operational efficiency.
The CFO Imperative: Redefining Assurance for Modern Finance
Redefining assurance in modern finance rests on two levers. Process redesign aligns controls to decision points such as approvals, overrides, and execution, ensuring risk is addressed at the moment financial decisions are made. Technology adoption enables this shift at scale, using automation, analytics, and AI to deliver timely risk signals and focus human judgment where it has the greatest impact. Together, these changes move assurance from a downstream check to an operational capability embedded in daily finance activity.
Cogneesol’s ADIS framework reflects this evolution through a deliberate “re-imagine, re-invent” approach to finance controls. It provides a structured way to operationalize process redesign and technology adoption, re-imagining assurance as continuous and re-inventing how automation, analytics, and human judgment work together. The result is stronger fraud resilience delivered without compromising governance discipline or execution speed.
The post Combating Financial Fraud: Mid-Market CFOs Need New Mechanisms appeared first on Cogneesol Blog.